Expert Corner: What Is Social Engineering Fraud and Why Is It on the Rise in 2024?
Rozy Setia, a Financial Crime Consultant at Ernst & Young Financial Services, discussed social engineering fraud for The Sumsuber Expert Corner.
Rozy Setia, a Financial Crime Consultant at Ernst & Young Financial Services, discussed social engineering fraud for The Sumsuber Expert Corner.
Fraud has become a significant concern in today’s digital world, posing a constant threat to personal information and financial systems. Recent data from the Federal Trade Commission reveals a stark increase in both the number of victims and the financial toll of fraud. In 2023 alone, 2.6 million consumers reported falling victim to fraudulent activities, with reported losses exceeding $10 billion.
Interpol, in its turn, reports a high prevalence of romance fraud and advanced payment fraud in the following regions:
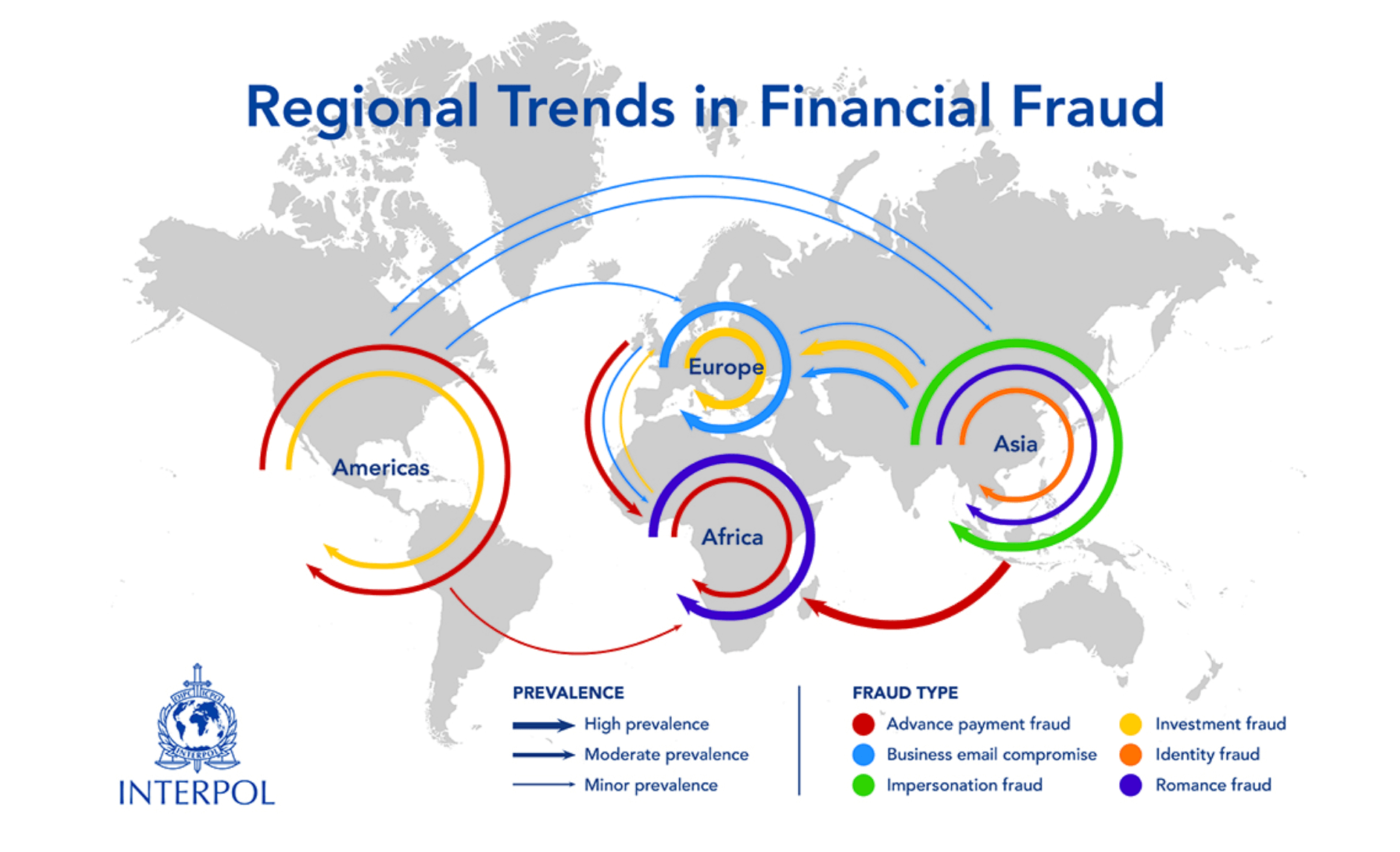
Source: Interpol
Most often, these types of fraud are a consequence of social engineering.
According to IBM’s 2023 Cost of a Data Breach report, data breaches initiated through social engineering techniques cost over $4.5 million on average.
According to Statista, in 2022, 30% of adults worldwide encountered phishing scams. In the same year, Vietnam had the largest share of internet users facing phishing attacks, and in the fourth quarter of 2022, there were over 1.35 million unique phishing sites worldwide.
Social engineering fraud, also known as “social engineering attacks” or “social engineering scams“, takes advantage of human emotions like fear, curiosity, or greed to deceive individuals or organizations into divulging sensitive information or performing actions that are detrimental to their interests.
Social engineering is the act of exploiting human weaknesses to gain access to personal information and protected systems. It relies on manipulating individuals rather than hacking computer systems to penetrate a target’s account. Social engineering attacks can happen to an individual online or in person, with the most common being phishing.
As our digital footprints expand, fraudsters find more personal and financial information to exploit, posing significant risks if not adequately protected. The consequences of fraud extend beyond immediate financial losses, potentially affecting victims’ credit ratings, personal relationships, and mental health. Perpetrators often use social media and other online platforms to gather information about their targets, making their schemes more convincing. Both businesses and individuals have fallen victim to social engineering fraud, leading to financial losses, data breaches, and compromised security. As technology evolves, so do the methods of fraudsters, making it essential for everyone to stay informed and proactive in protecting themselves against social engineering attacks.
Social engineering refers to the manipulation of a target to elicit key information. In addition to stealing an individual’s identity or compromising a credit card or bank account, social engineering can be applied to obtain a company’s trade secrets or exploit national security.
For example, a woman might call a male victim’s bank, pretend to be his wife, claim an emergency, and request access to his account. If the woman can successfully socially engineer the bank’s customer service representative by appealing to the representative’s empathetic tendency, she may succeed in obtaining access to the man’s account and stealing his money. Similarly, an attacker might contact an email provider’s customer service department to obtain a password reset, making it possible for the attacker to control a target’s email account rather than hacking into that account.
Attackers often use surprisingly simple tactics in social engineering schemes, such as asking people for help. Another tactic is to exploit disaster victims by asking them to provide personally identifiable information such as maiden names, addresses, dates of birth, and social security numbers for missing or deceased loved ones. Why? Because these pieces of information can later be used for identity theft.
Posing as a technical support professional or a delivery person is an easy way to gain unauthorized access to an account, as is sending a seemingly legitimate email with a malicious attachment. Such emails are often sent to a work email address where people are less likely to be suspicious of an unknown sender.
Emails can be disguised to appear as though they have originated from a known sender when they are actually sent by a hacker. More elaborate tactics targeted at specific people might involve learning about their interests and then sending the target a link related to that interest. The link can contain malicious code that can steal personal information from their computers. Popular social engineering techniques include phishing, catfishing, tailgating, and baiting.
Phishing is an attempt to steal sensitive information, typically in the form of usernames, passwords, credit card numbers, bank account information, or other important data in order to utilize or sell the stolen information. Phishing and pretexting are prevalent forms of social engineering fraud, where perpetrators send deceptive messages or create false scenarios to trick victims into providing sensitive information.
Catfishing is when a person takes information and images, typically from other people, and uses them to create a new identity for themselves. In some cases, a catfisher steals another individual’s complete identity—including their image, date of birth, and geographical location—and pretends that it is their own.
Tailgating is a form of social engineering attack where an unauthorized individual breaches a company’s security system to physically access, steal, or compromise its data.
Baiting is a type of social engineering attack where a scammer uses a false promise to lure a victim into a trap that may steal personal and financial information or infect the system with malware. The trap could be in the form of a malicious attachment with an enticing name.
Emotional manipulation is another common tactic used by social engineers, who exploit fear, greed, curiosity, or sympathy to manipulate their victims into complying with their requests.
Social engineering fraud can take various forms and exploit cultural nuances, technological vulnerabilities, and socio-economic factors unique to each region. Here are some common types of social engineering fraud prevalent globally:
Phishing: This is a widespread form of social engineering where attackers send deceptive emails or messages pretending to be from reputable organizations or individuals to trick recipients into revealing sensitive information such as passwords, credit card details, or personal information. Phishing attacks often target employees of multinational corporations, government agencies, or financial institutions.
Recently, Interpol announced that law enforcement agencies from 19 countries had significantly disrupted one of the world’s largest phishing-as-a-service platforms, LabHost. This platform was a major resource for cybercriminals globally, offering monthly subscriptions that included phishing kits, hosting infrastructure, interactive tools for victim engagement, and campaign management services. The investigation revealed at least 40,000 phishing domains associated with LabHost, which had approximately 10,000 users worldwide.
Online baiting: Online baiting occurs when hackers send out ads with links that look like opportunities to find jobs, earn side money, or provide useful information. When an unsuspecting person clicks on the bait, malware infects their computer.
Physical interactions: Social engineering attacks don’t just happen online. Physical interactions can occur, such as when an individual pretends to work in your office and asks you to let them in because they “forgot the door code or their card key” and need help.
Business Email Compromise (BEC): Also known as CEO fraud, this involves attackers impersonating high-level executives or business partners to deceive employees into making unauthorized transactions or disclosing sensitive information. Businesses, especially those with operations in multiple countries, are prime targets for BEC scams due to language barriers and communication complexities.
According to the SlashNext 2024 report, BEC attacks have increased by 29%. Some of the most prevalent types of BEC threats include gift card scams (21%), social engineering investment scams (16%), purchase renewal scams (14%), social engineering beneficiary scams (12%), and social engineering donation scams (10%).
Impersonation scams: Attackers impersonate trusted individuals, such as government officials, law enforcement officers, or tech support personnel, to manipulate victims into providing personal information or transferring money. These scams often exploit cultural norms and hierarchical structures to intimidate victims or gain their trust.
Ransomware: While not strictly social engineering, ransomware attacks often involve social engineering tactics to trick users into downloading malicious software. Ransomware attacks have targeted organizations across various sectors, including healthcare, finance, and government, leveraging social engineering techniques tailored to regional preferences and languages.
Voice phishing, or vishing: Attackers use phone calls or voice messages to impersonate trusted individuals or organizations and deceive victims into providing sensitive information or transferring funds. Vishing attacks may exploit linguistic diversity and dialects to appear more convincing to victims.
Real case 1: In 2019, criminals used AI-based software to impersonate a chief executive’s voice and demand a fraudulent transfer of €220,000 ($243,000).
Real case 2: In 2023, a 59-year-old woman lost Rs 1.4 lakh ($1.6K) to an AI voice scam. The caller skillfully emulated her nephew based in Canada and concocted a distressing story, asserting an urgent need for immediate financial aid.
Online romance fraud: Also known as romance scams, this type of social engineering fraud involves perpetrators creating fake personas on dating websites, social media platforms, or online forums to establish romantic relationships with unsuspecting individuals. Once trust is established, the fraudster exploits the victim’s emotions and goodwill to extort money or personal information.
Real case: Just recently, a Long Island woman lost more than $400,000 in a romance scam—and then was scammed again when she went looking online for help to get her money back.
Romance scams usually involve the following steps:
Online shopping scams: Scammers create fake e-commerce websites, apps, or ads offering heavily discounted products, but the purchased items are never delivered or are counterfeit or of poor quality.
Real case: Last year, a 70-year-old woman from Mumbai lost Rs 8.3 lakh ($9.9K) while shopping online. She was making a purchase of Rs 1,169 online; however, Rs 19,005 was debited from her account. She called the bank helpline number but later got duped for a total of Rs 8.3 lakh.
Tech support scams: Scammers pose as representatives from well-known tech companies, claiming to have detected issues with the victim’s device and offering to fix the problem in exchange for payment or remote access to the device.
Pig butchering scam: Also known as a “sha zhu pan” scam, this type of online investment fraud involves scammers creating fake online personas to lure victims into fraudulent investment schemes. The term “pig butchering” comes from the scammers’ practice of “fattening up” their victims by building trust over time before “slaughtering” them and stealing their money. These scams, which often originate overseas and involve cryptocurrency “investments,” have become a global problem, with several billions of dollars in reported losses worldwide.
Real case: Just this year, a man lost more than $500,000 after falling victim to an online scam known as “pig butchering”. She called herself Anna and connected with Barry May on Facebook, claiming to be an Asian woman living in New York. She convinced him to invest over $500,000 in cryptocurrency, promising they could be together and he would see huge returns, but it was all a scam. Just before he took out a loan to send more money, an FBI agent informed him that he was a victim of major fraud.
Social engineering attacks are illegal, and some forms, such as identity theft or breaking into a government facility, are considered serious crimes. Employee training, robust authentication mechanisms, information security policies, technological defenses, incident response plans, vendor and partner security, cultural measures, physical security, and regular audits and reviews are all critical components of a comprehensive security program.
To effectively protect against social engineering tactics, companies should regularly introduce the following practices:
The sophistication of social engineering attacks is increasing, making robust preventive measures essential. Adopting a proactive approach that emphasizes education and awareness is crucial for individuals and organizations to recognize and respond to potential threats. Regular training sessions, simulated attacks, and up-to-date information on the latest tactics can fortify human defenses against such manipulation.
In addition to human defenses, implementing stringent security policies, employing multi-factor authentication, and maintaining regular system updates are crucial technical defenses. However, the human element remains the most vulnerable link in the security chain. Therefore, fostering a culture of vigilance and skepticism is essential.
To combat social engineering fraud, a dual approach is necessary: enhancing both technological defenses and human awareness. As attackers continue to refine their methods, continuous education and adaptability will be key to safeguarding sensitive information and maintaining trust in the digital realm. Stay informed and stay vigilant.