- May 22, 2024
- 6 min read
3 Ways to Prevent Identity Theft in 2024
Learn about identity theft and how to protect against it in 2024.

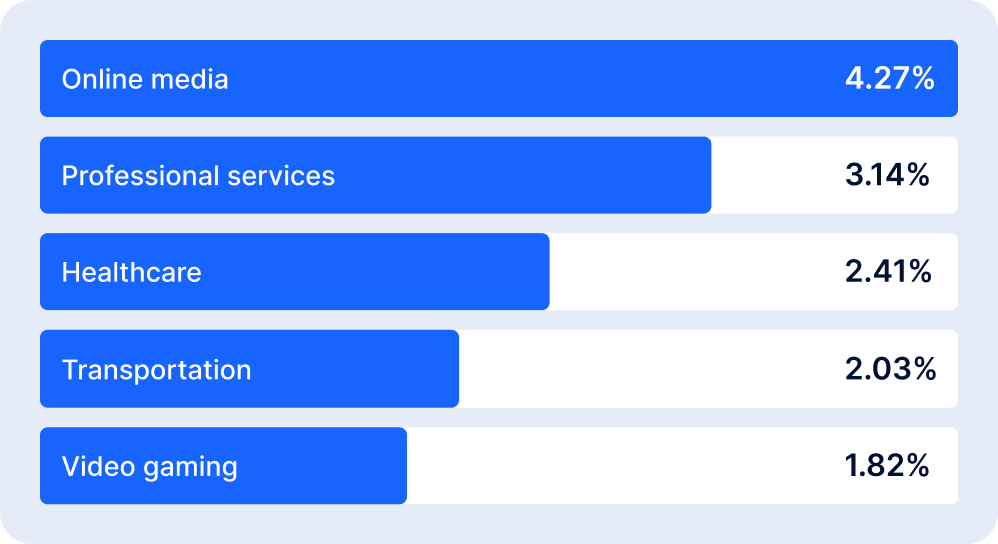
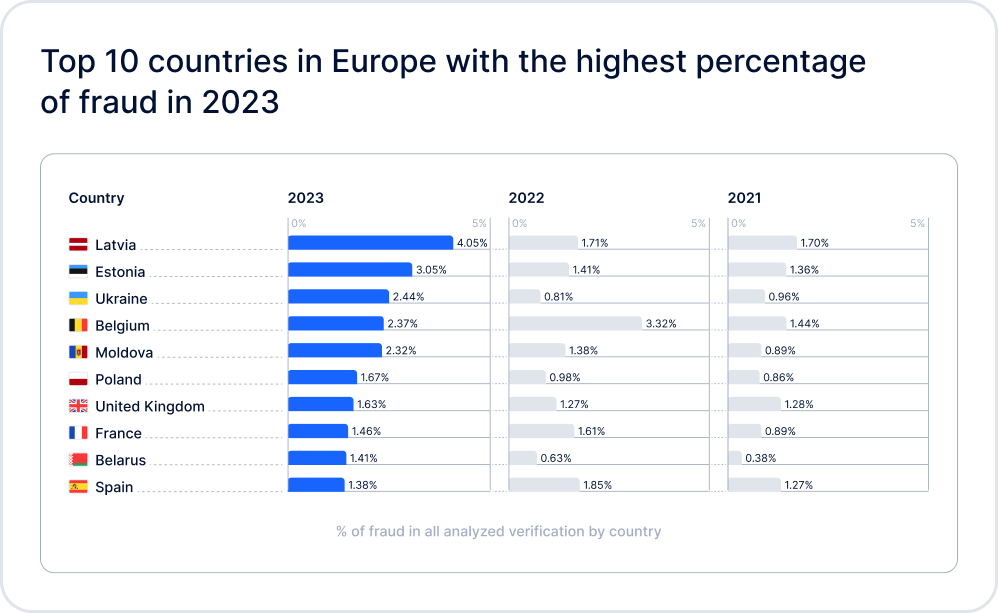
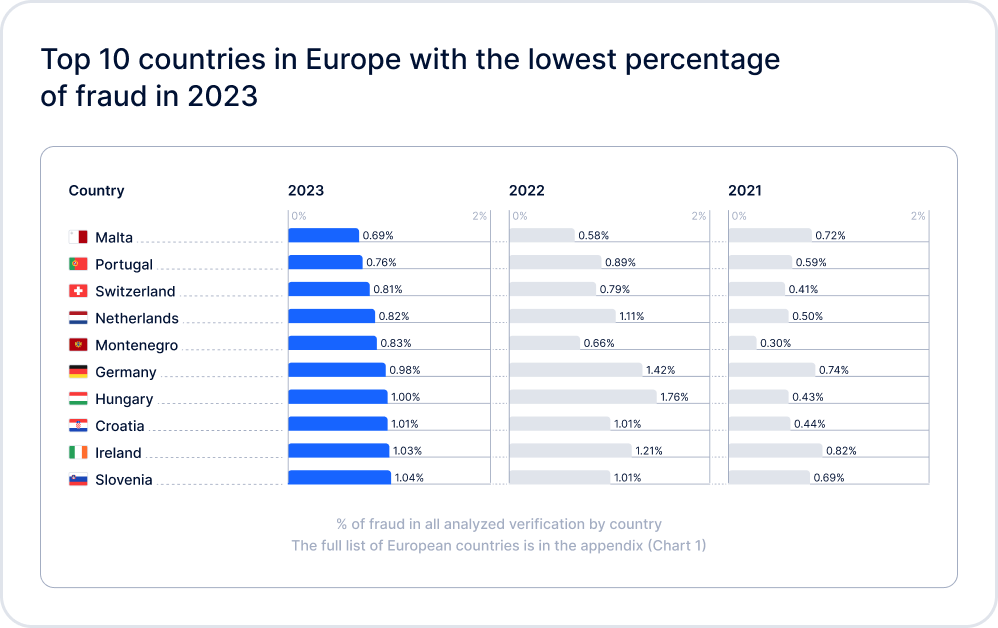
According to Sumsub’s 2023 Identity Fraud Report, fraud is not only increasing in number; it’s also getting more sophisticated. Even documents from developed economies were increasingly forged by fraudsters, with ID cards remaining the most frequently exploited for identity fraud (accounting for nearly 75% of all fraud involving identity documents). The most affected industries in 2023 were online media, professional services, healthcare, transportation, and video games.
Here you can see the fraud highlights for 2023.
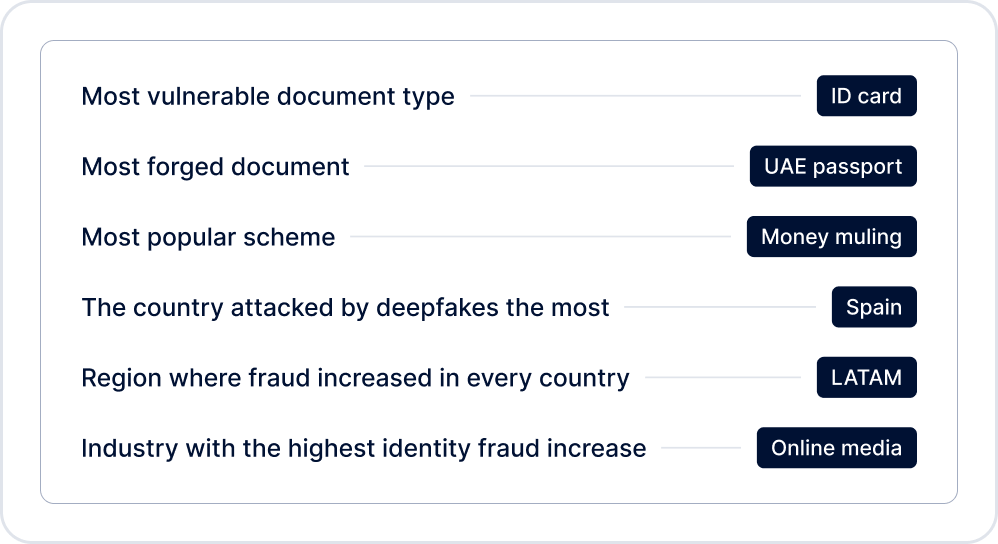
Fraudsters will seize any opportunity to gather sensitive data to use for identity fraud. However, with the right anti-fraud controls in place, companies can avoid having to deal with false bank accounts, fake licenses, unpleasant headlines, and police investigations.
In this article, we’re going to cover the most common identity theft types and how to protect against them.
What is identity theft?
Identity theft is when personal information—such as name, date of birth, address, bank account, emails—is stolen to make purchases, open accounts, withdraw money and get tax refunds. This allows fraudsters to use their victim’s identity for illicit purposes.
How fraudsters steal personal data
Be it through cyber attacks or data leaks, identity thieves often target small and medium-sized businesses to scavenge personal data, which leads to significant reputational damage and losses. Last year, the FBI Internet Crime Complaint Center (IC3) released a Public Service Announcement, identifying nearly $51 billion in exposed losses due to business email compromise between October 2013 and December 2022.
Fraudsters can target individuals directly by stealing mail or scavenging personal information on Facebook, Twitter or Instagram. They can also hack emails, bank accounts, or buy data from the “dark web”.
Here are the most common identity theft methods:
- Physical theft. Theft of documents that have a name, address, account number or any other sensitive information, such as credit cards or bank statements.
- Phishing. Fraudsters send emails pretending to be a legit company, agency or organization, asking victims to share personal information, name, address, card or bank account details, passwords, etc.
- Cold calling. Fraudsters call their victims posing as bank support or other service providers to trick them into sharing personal information.
- Hacking. Criminals break into computer systems to steal identity and credit card details, banking data, etc.
- Inside jobs. Employees can abuse their positions at banks or other institutions to sell customer data on the dark web.
7 common targets of identity theft
- Financial information. Thieves use stolen personal data to access peoples’ finances, or create new accounts under someone else’s name. A syndicate in Melbourne used stolen personal data to open 70 accounts at various banking institutions. They later withdrew the money overseas and transferred it back to Australia through cryptocurrencies.
- Driver’s licenses. Thieves obtain a driver’s license in another person’s name for the purpose of traffic violations or vehicle theft. San Francisco-based luxury car-sharing service, HiGear, learned this lesson the hard way, when it was forced to shut down due to identity fraud related theft incidents.
- Social security numbers. A SSN number can be used to steal the social security benefits of other people. They can also be used to obtain sensitive documents, take out loans or apply for credit cards. Cybercriminals used a fake Citibank website to steal debit cards and SSN in order to access bank accounts.
- Medical information. Stolen medical records can be used for health insurance and medical coverage fraud. As a result of a massive cyber attack in Singapore, criminals stole the personal data of 1.5 million patients, including names, NRIC numbers, addresses, gender, race, date of birth, and medical history.
- Tax identity. Once criminals get hold of people’s tax information, they can use it to file false tax returns or refunds. Two Florida men used personally identifiable information to file fraudulent tax returns using their tax preparation services firm.
- Employment information. Fraudsters can assume someone else’s identity to collect public benefits. An unknown Massachusetts man used a stolen identity for 40 years.
- Child identity. Childrens’ personal data and SSNs can be used to obtain documents, apply for loans and even credit cards. In Portland, a nine-year-old’s identity was used to open a bank account and credit card.
Fortunately, fraudsters also make mistakes, and there are ways to stop them before they try to hurt customers and businesses.
Red flags of identity theft
- Unfamiliar credit card charges or charges on bank statements
- Unfamiliar or abnormal medical bills, files
- Bills from unfamiliar companies
- Confirmation emails for purchases not made
- Confirmation emails for accounts never created
- Debt collectors contacting you about outstanding bills which are not yours
- Receipt of credit cards which you didn’t order
- Notification of approval or rejection for credit cards you didn’t order
- Suspicious login attempts to your online accounts, including social media
- Fraud alerts from online services
- Sudden drop in your credit rating
- Credit or loan rejection despite clean credit history.
How to prevent identity theft
Being aware of blind spots and incorporating certain practices can considerably reduce the risks of fraud. Below we share some advice on secure methods of identity theft prevention for businesses and their customers.
1. Protect sensitive data
- Encrypt data. Securely encrypt customer data before transmitting or storing it. This includes credit card, bank account and social security information.
- Use a firewall, secure VPN and updated software. Install a firewall and a reliable VPN to fight off hackers. Make sure to perform regular system updates to fix security issues.
- Limit access to key personnel. Give access only to those employees that work with personal data; shred old business records.
- Adopt new technology. This can include antivirus software, encrypted backups, or DDoS appliances.
- Check the vendors you work with. Make sure you are putting sensitive data in the hands of companies that know how to protect it.
2. Establish data protection policies
Develop and incorporate guidelines on how your business handles and stores customer information—including how the business accepts payments and performs client identification.
- Engineer a step-by-step protocol for data breaches.
- Appoint an information security officer
- Set deadlines for record keeping, including how long the company has to store client information.
- Get rid of excess sensitive data that isn’t vital to the customer’s account.
- Do not store SSNs, driver’s licenses or birth dates online, if possible.
3. Set customer identification rules
- Request ID. Ask for ID when customers pay by card. This allows you to compare their ID information with the name on the credit card.
- Recheck user IDs when there’s a change in payment data or the user profile to verify that the client’s account has not been taken over.
- Use multi-factor authentication which combines several verification approaches.
- Use Liveness Detection to ensure that the applicant is real and present during verification.
- Don’t collect unnecessary data. If you are not going to use the customer’s address or birth date, there is no need to request it at all.
- Establish fraud alerts and inspections. Use security freezes when the system detects suspicious activity. Manually review unusual transactions if necessary.
Fraud incidents lead to many consequences, including law enforcement investigations and chargebacks, meaning financial and reputational losses for the business.
Security is key to the success of any financial business—especially those that deal in the personal data of thousands or millions of people. Businesses should focus on their internal practices and study their security needs step by step as there is no defense that suits all.
Identity theft statistics for 2023
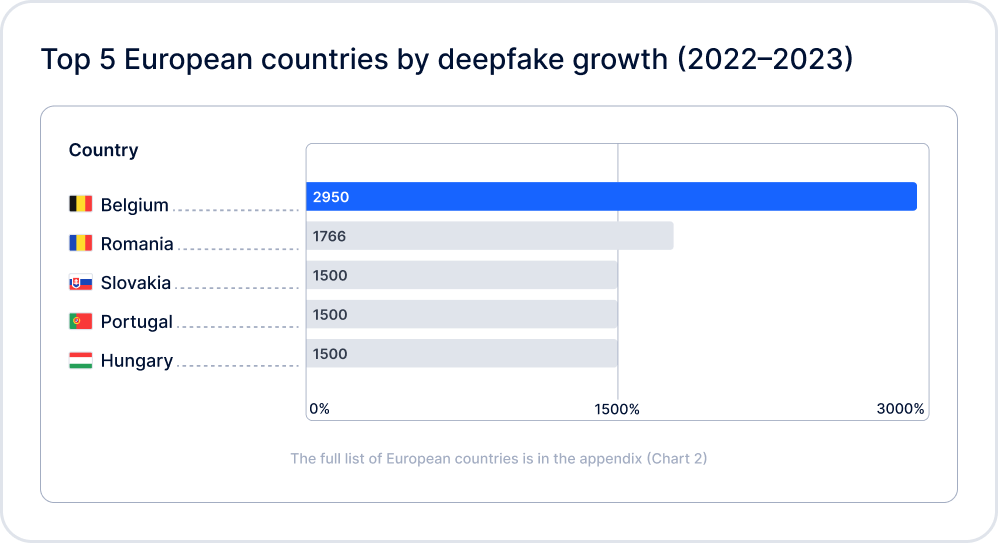
2023 saw a continuation of the trends established in prior years. In Sumsub’s Identity Fraud Report 2022, the top 3 fraud trends identified were deepfake usage, complex fraud patterns, and advanced forgeries. In 2023, these trends not only persist, but also continue to evolve dynamically. The most popular identity fraud types of 2023 include:
- AI-powered fraud (mainly deepfakes)
- Money mulling networks
- Fake IDs
- Account takeovers
- Forced verification
Subscribe to continue reading
Enter your email address to get access to the full article
Relevant articles
- Article
- Jun 6, 2025
- < 1 min read

- Article
- 3 days ago
- 7 min read
Everything you need to know about the #1 defense against fraudsters and money launderers.