AML Transaction Monitoring Rules & Scenarios 2024
Learn about rule building, red flags, and indicators of suspicious behavior in transaction monitoring.
When it comes to transaction monitoring, rule building is crucial. Among other things, rules separate customers into categories, allowing businesses to more effectively monitor customer behavior.
To simplify the rule building process, we at Sumsub have prepared this guide discussing the different scenarios companies need to be prepared for.
Rule building for transaction monitoring
Compliance teams establish lists of scenarios that could be deemed “suspicious” based on certain parameters (which we’ll get into in the following sections). The purpose of these lists is to create alarms that notify staff members when suspicious transactions occur, so they can take action. These alarms are known as “rules” or “AML scenarios”.
Examples of AML scenarios
Firms subject to AML rules need to first understand what specific risk factors they should take into consideration when conducting ongoing monitoring of client activity. Some of these include:
- The client’s behavior, such as refusal to provide requested information, unusual transactions, exceeded thresholds.
- The client’s reputation
- The risk inherent to the asset or service being acquired
- Unusual transactions or exceeded thresholds
- The consistency of client profile information
- Whether sources of funds appear legitimate
- Whether transactions involve sanctioned entities or Politically Exposed Persons (PEPs)
You can learn more about AML red flags here.
How to create effective rules: use cases
Use case: transaction monitoring
Sumsub recommends looking at the following indicators when creating rules for transaction monitoring:
- Location. For example, multiple purchases made with the same credit card in different countries over a short period of time or activities conducted by multiple individuals using the same IP address.
- Sequence. For example, a series of transactions below a certain threshold, deposits succeeded by withdrawals within a short timeframe, or multiple purchases of high-value items followed by quick returns.
Thresholds can be set on a daily, weekly, monthly, quarterly or even yearly basis.
- Destination. For example, a large sum of money transferred to a high-risk country or high-risk individual/legal entity included within sanction lists or adverse media.
Use case: payment errors and refunds
Companies should also create rules to detect payment processing errors and initiate refunds if needed. This includes:
- Incorrect transaction amounts
- Duplicate charges
- Issues with provided personal information
Use case: preventing hacks
Companies can also use rules to prevent unauthorized access to users accounts and other fraudulent activity, zeroing in on:
- Logins from unusual devices and high-risk locations
- Frequent changes of account information or shipping address
- Multiple failed login attempts within a short period of time
- Creation of multiple accounts using a single IP address
Use case: compliance with regulations
Companies can also protect their users and revenue by taking additional measures to comply with regulations:
- Create lists to block transactions from sanctioned entities
- Add AML screening for large transactions
- Introduce additional checks, such as biometric authentication, if suspicious behavior is detected
- Leverage crypto analytics and Travel Rule checks for crypto transactions
Example
A company has to report all transactions exceeding $3,500. It should therefore set an AML rule that is triggered if a customer deposits or withdraws $3,500 or more in 24 hours.
It should be noted that criminals can split their transactions into several smaller ones to avoid being caught. This technique is called smurfing. The people moving these smaller amounts – known as smurfs – will often spread the transactions over various accounts to keep them under regulatory reporting thresholds and avoid detection.
Below is an example of how you can proactively stop smurfing. This AML rule compares ingoing and outgoing transactions and checks if a withdrawal amount is 10% less than the original deposit amount. This is a tell-tale sign of money laundering because the third party participant (e.g., money mules) is usually paid a percentage for their efforts.
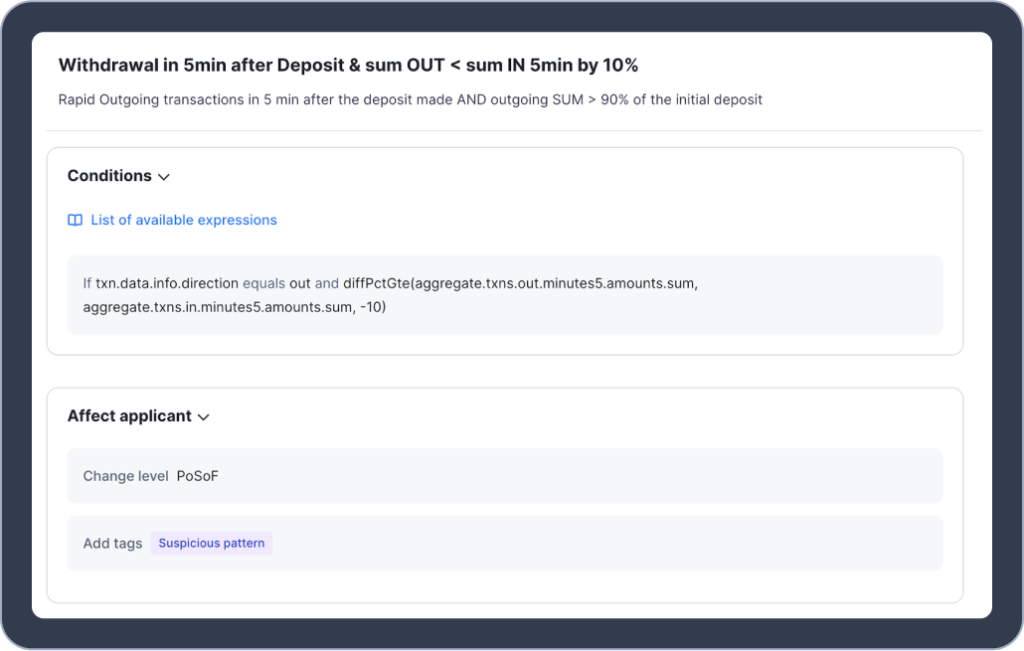
This rule can trigger one or both of the following automated actions:
- Customer is asked to provide proof of Source of Funds
- Customer is assigned a tag that will show if further transactions are made
In the rule below, you can see how the conditions can be altered if customers attempt to initiate multiple outgoing transactions within a certain time period after registration:
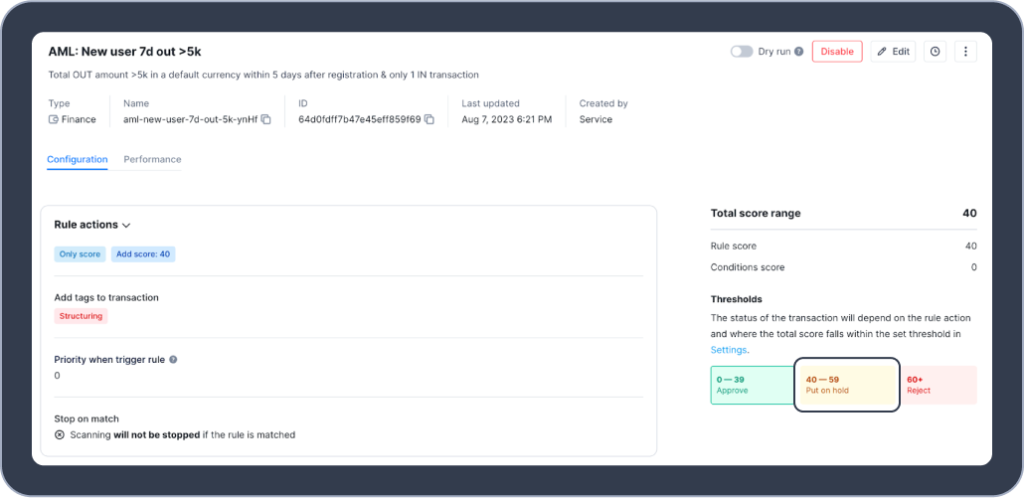
If the above rule is triggered, a higher risk score will be assigned to the customer and, based on the threshold settings, the transaction status will change to “put on hold”.
AI for advanced monitoring
Artificial Intelligence (AI) has recently become an integral part of transaction monitoring, spotting patterns that humans might overlook. AI technology can also process large amounts of information and spot suspicious transactions (e.g., split transactions).
Automated transaction monitoring software
The larger a company gets, the more resources it needs to allocate to transaction monitoring. And sooner or later, it simply becomes inefficient to use manual work. That’s when automated solutions come into play.
Automated software can simplify the workflow by monitoring multiple transactions simultaneously. And if a complex case arises, it can be sent for manual review. Otherwise, most transactions are checked automatically. This approach maximizes the number of approved transactions, while keeping the company compliant with the regulations.
Sumsub’s Transaction Monitoring algorithms use complex analytic models to differentiate between legitimate and fraudulent activities. The solution analyzes transactions based on the predetermined rules, sending potentially risky transactions for manual review. As soon as such a transaction is put in the queue, a webhook action is sent to the company’s compliance team.
FAQ
-
What are transaction monitoring rules?
Transaction monitoring rules are a set of criteria that allows companies to spot suspicious transactions. Each company can create its own set of rules, as long as it allows them to comply with regulations.
-
What are scenarios in AML transaction monitoring?
Some of the most common scenarios considered in transaction monitoring include:
- The client’s behavior, such as refusal to provide requested information, unusual transactions, exceeded thresholds.
- The client’s reputation
- The risk inherent to the asset or service being acquired
- Unusual transactions or exceeded thresholds
- The consistency of client profile information
- Whether sources of funds appear legitimate
- Whether transactions involve sanctioned entities or Politically Exposed Persons (PEPs)
-
What are transaction monitoring alerts?
Transaction monitoring alerts notify companies about suspicious activity. Whenever such an alert is triggered, transactions should be blocked followed by an investigation. The employee detecting the suspicious activity should escalate the incident to a compliance/AML officer or senior management to decide whether a Suspicious Activity Report (SAR) should be filed to the relevant Financial Intelligence Unit (FIU). If it is decided to not to file a SAR, the reasons for doing so must still be explained.
-
What is a false positive AML alert?
False positives occur when legitimate transactions are marked as suspicious. To avoid this, company’s should should diligently build out their AML scenarios and hire a reliable solution provider.







