- Jun 04, 2021
- 7 min read
How to Onboard Users in the 250 Million Strong Post-Soviet Market
As one of the largest regions in the world, the Commonwealth of Independent States (CIS) region holds many opportunities for businesses. However, companies risk facing regulatory sanctions if they don’t consider local specifics when onboarding users. Penalties may include hundreds of thousands of dollars in fines or total seizure of business activity.
Also, as the US, the UK and the EU have imposed a wide range of sanctions on Russian entities and elites due to Russo-Ukrainian crisis, proper user and corporate verification has become a must for businesses.
This article provides best practices for performing KYC checks on CIS customers that can help to avoid sanctions and fraud.
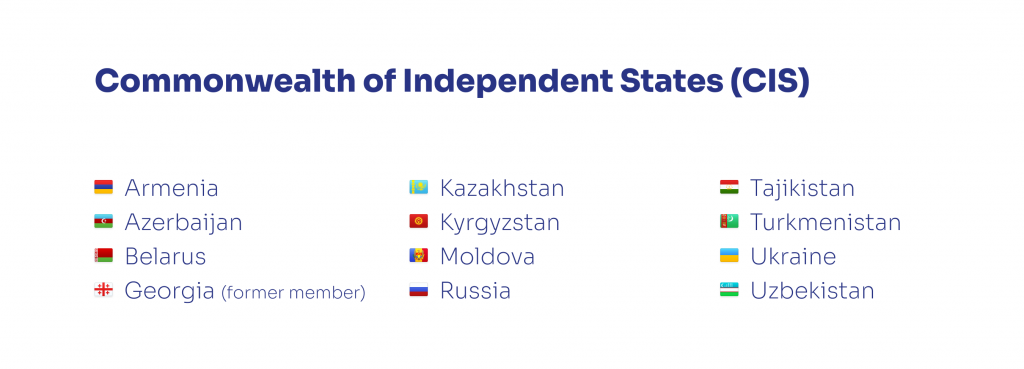
 The CIS is an intergovernmental organization that oversees economic and political cooperation between ten post-Soviet republics: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, and Uzbekistan. In this article, we’ll also cover Ukraine and Georgia, former CIS members.
The CIS is an intergovernmental organization that oversees economic and political cooperation between ten post-Soviet republics: Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, and Uzbekistan. In this article, we’ll also cover Ukraine and Georgia, former CIS members.
Who’s concerned
Businesses that onboard customers in the CIS region should consider AML and data protection obligations of the member countries.
The degree of compliance depends on whether a business is registered in the CIS. If a company has set up a legal entity in one of the states, then it must comply with all local laws. However, if a company onboards CIS customers but isn’t registered in the region, it must only meet data protection requirements.
Why it’s important to consider CIS laws
For international businesses, it may be tempting to create a single onboarding flow for customers across different jurisdictions. However, not taking into account CIS-specific regulations can result in administrative and criminal sanctions.
For instance, in Uzbekistan, unlawful data processing leads to the seizure of business activity. In Belarus, penalties include three years imprisonment. And in Russia, authorities can slow down or even block a company’s website for data breaches. In severe cases, Russia may impose fines of up to 18m RUB (over 240 thousand dollars).
With Sumsub, you don’t have to worry about your compliance obligations. Talk to our team today.
How to onboard users
AML laws in CIS countries require businesses to identify and verify their customers. Both remote and non-remote verification is allowed in all member states, and there are no unique requirements, such as selfie-based or video KYC. This means that businesses can align their CIS onboarding flow with other jurisdictions.
To mitigate risks at the verification stage, businesses should pay attention to the five regional specifics below.
High fraud risk. Proper KYC checks are a must in the CIS due to the high level of fraudulent activity in the region. In 2020, criminals stole 2 billion dollars through online fraud in Russia alone.
Even the largest financial platforms are victims of fraud. For instance, in 2020, Vladimir Plahotniuc, a prominent Moldovan politician, was accused of stealing $1 billion from Moldova’s three largest banks. Other common fraud schemes include concealment of funds abroad as well as the use of payment systems that permit unauthorized transfers.
Complex politics. Sanctions screening of CIS customers should be a priority for businesses, as there is a large number of sanctioned oligarchs and politicians that try to launder money abroad.
As the 2020 FinCEN files leak revealed, wealthy officials from post-Soviet states have laundered billions of dollars through major global banks. Among them is Andriy Klyuyev, an adviser to former Ukrainian President Viktor Yanukovych. He was sanctioned by the EU in 2014 but continued laundering funds through American banks up to 2015.
On February 24th, 2022, Russian President Vladimir Putin announced a “special military operation” in Ukraine. In response to this, the US, EU and other countries have imposed sanctions on Russia.
Limited coverage by AML providers. While database coverage is substantial in the region—reaching 99% in Belarus and Russia—many international AML providers don’t have access to local databases. Therefore, businesses should ensure that their KYC & AML provider has the necessary access.
Unique data protection obligations. Businesses must store the personal information of users from Kazakhstan, Russia, and Uzbekistan on servers located in these countries. For instance, a UK-based company onboarding customers from Uzbekistan cannot keep their users’ data in the UK—only in Uzbekistan.
Non-Latin writing systems. The majority of CIS countries use non-Latin writing systems, including Cyrillic (Belarus, Russia, Ukraine, etc.), Georgian, and Armenian scripts. Therefore, businesses must employ user verification technology with OCR (Optical Character Recognition) that can process and convert documents written in non-Latin characters.
Now, let’s dive deeper into the types of ID documents in the CIS region and how to screen them.
How to check documents
To onboard CIS users, businesses should be prepared to deal with unique types of identity documents. For instance, in Russia and Ukraine, there are both internal passports and travel passports—a system that dates back to the Soviet period. Other specific documents include the seafarers’ identity document of Ukraine and the military IDs of Belarus, Kyrgyzstan, and other member states.
To ensure high conversion rates, businesses should be able to process the following document types:
- internal passports
- travel passports
- driving licenses
- ID cards
- military ID documents
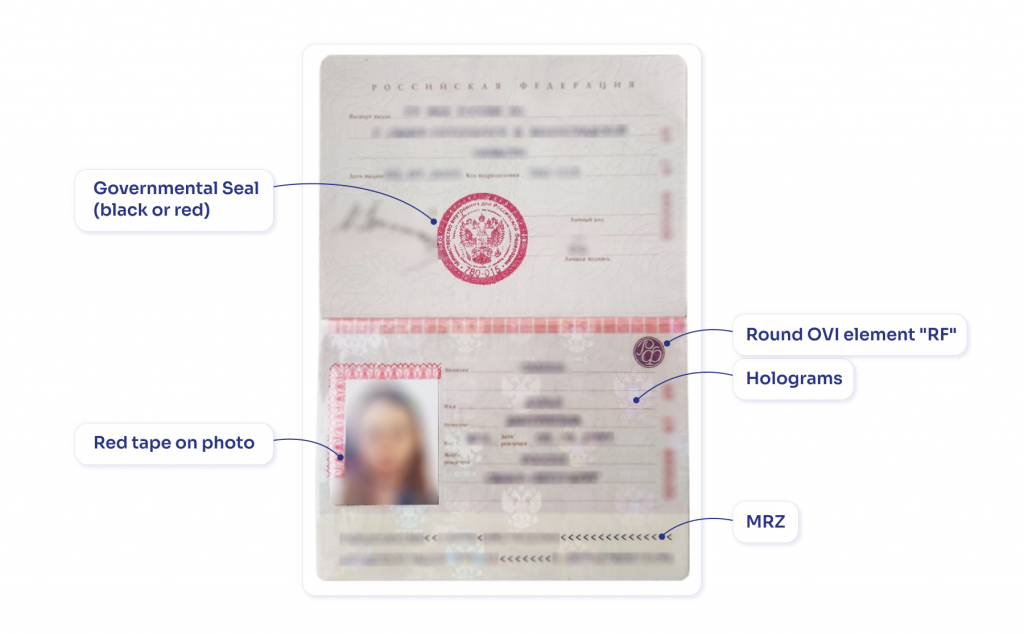
Some ID documents (e.g., old Ukrainian passports) have low security and can easily be forged. Here are some tips that can help for detecting altered documents:
- Compare documents with official templates. Use templates of official documents to ensure that all elements of a user’s document are in the right place. Check out PRADO’s website for official templates of CIS travel passports.

- Check security features. Since the human eye can’t always notice tampering, we recommend using AI-powered systems to screen user profiles and recognize security features on documents, such as watermarks, holograms, seals, etc.

- Validate MRZs (Machine-Readable Zones). An MRZ is a codified element of an identity document that facilitates automated scanning of personal data. However, older ID documents usually don’t contain MRZs, which makes them less secure and requires businesses to pay more attention to screening.
Suggested video: Still not convinced why you should properly screen security features and MRZs on documents? Check out our YouTube video:
How to check users against databases
In most jurisdictions, databases are either unavailable or unreliable. However, in the CIS, database coverage can be as high as 99% (as is the case in Russia), which can be quite useful for verification.
Here are the two types of databases that businesses can acquire:
- AML databases (global watchlists, PEP and sanctions lists, adverse media, etc.). Although PEPs and sanctions screening in the CIS region is a must (given the large number of corrupt officials), it’s extremely difficult to find domestic PEPs and sanctions lists. Therefore, businesses should rely on international AML lists and adverse media checks for verifying CIS users.
- Databases for identity verification (credit bureaus, governmental and consumer databases). Although some CIS countries (Armenia, Belarus, Russia, and Moldova) allow identifying persons solely through governmental databases, this doesn’t provide the necessary protection from fraud.
Verifying identities through credit bureau databases also poses significant risks. Let’s take a look at a popular fraud scheme that illustrates the vulnerabilities of these databases:
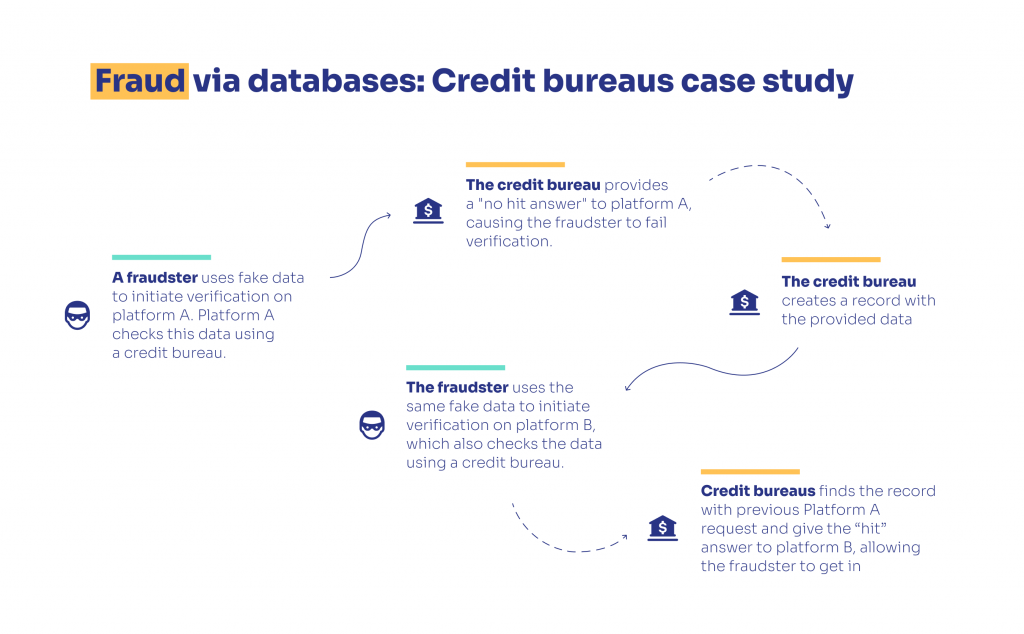
All in all, database screening can be a useful additional step for verifying CIS users—but businesses shouldn’t solely rely on it.
Acquiring a database in the region can be a lengthy and expensive process. The expenses are not due to check costs, but rather the need to set up a legal entity in the country in order to use governmental databases. Therefore, it can be more cost and time effective to reach out to a provider.
How to build the most secure onboarding for CIS users
To trick financial businesses, sophisticated fraudsters don’t just use falsified documents. Instead, they buy real ones on the darknet. So even the most reliable systems won’t detect anything suspicious because no document manipulation has occurred.
Therefore, businesses should introduce a combination of approaches that ensure that the true document holder undergoes verification.
Here’s Sumsub’s take on the most secure and efficient onboarding:
Automated document screening. Introduce a reliable system that checks documents and detects alterations. Ensure that it can process Cyrillic, Armenian, and Georgian characters. Automated solutions are preferable since most services in the CIS are digital and users are accustomed to fast remote verification.
Database checks. Have access to governmental databases, PEPs, sanctions lists, and internal blocklists of other platforms. Since there is a high number of fraudsters forging documents in the CIS, businesses should use database screening as an additional step to ensure tip-top secure onboarding.
Facial biometrics. Employ liveness technology to ensure that the true document holder is present during the KYC check. This prevents fraudsters from using masks or deepfakes to get verified.
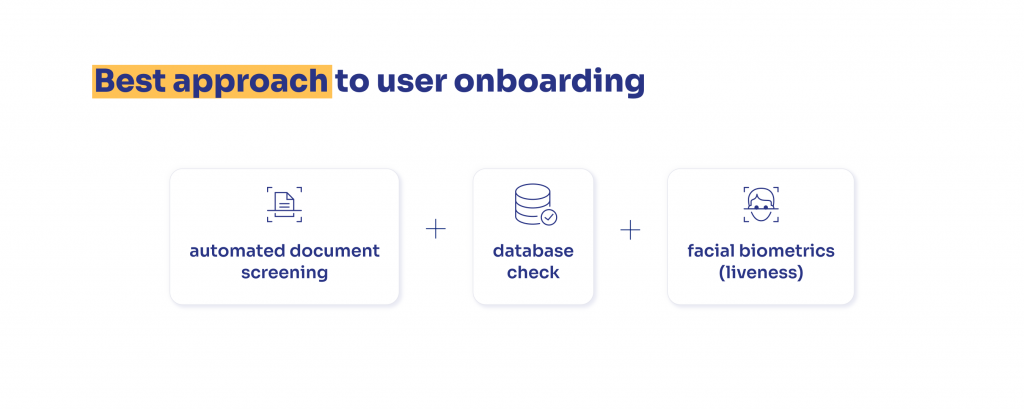
All in all, a secure onboarding process should include a combination of approaches, such as image authenticity analysis, database screening, and biometric checks.
How to store user data
To recap, businesses must store the personal information of users from Kazakhstan, Russia, and Uzbekistan locally. So, if a business has Uzbek customers, it must only keep their data in Uzbekistan. Businesses shouldn’t neglect this requirement since non-compliance can result in enormous fines.

To store data locally, businesses can rent servers in the relevant country. CIS states other than Kazakhstan, Uzbekistan, and Russia do not require local data storage—all that matters is that personal data is kept securely.
If a business uses a KYC provider, the provider must:
- Store data locally for users from Kazakhstan, Russia, Uzbekistan
- Be listed in national registries of data processors (otherwise, providers cannot process user data in these countries)
- Use data protection means, including data encryption mechanisms.
Cross-border transfers of personal data are possible but require consent from users in written form. However, there are a number of countries that businesses can transfer data to without prior consent. These include Germany, the UK, and other states that belong to the Convention for the Protection of Individuals with regard to Automatic Processing of Personal Data.
Key takeaways
Businesses can build unified onboarding flows for users in the CIS and elsewhere, as there are no unique requirements for remote verification in this region.
To avoid regulatory sanctions, businesses should ensure that their onboarding process is fully compliant, paying extra attention to data protection obligations as breaches can result in the seizure of business activity and extremely large fines.
Given the widespread of corruption, fraud, and money laundering in the CIS, it’s best to take an onboarding approach that includes not only document verification but also database screening and biometric checks.
Following these principles, companies will be able to expand into the growing CIS market, acquiring more customers and staying protected from fraud.
With Sumsub’s holistic KYC & AML solution, you can onboard users instantly. Request a demo today.



