- Dec 27, 2022
- 7 min read
Blockchain, Digital Identity, and the Next Level of Data Security
Learn about blockchain, its role in securing digital identity, and why the technology may be a step forward in personal data security.
Blockchain may soon completely change the way we interact in the digital world, including how we store and share data. The technology has many uses, but one of the most promising areas is digital identity management.
In 2022 alone, millions of people around the world suffered personal data leaks. This has increased the need for secure methods of storing, transmitting and verifying personal information. Blockchain technology can offer a solution.
In this article, we explore how blockchain came to be and its impact on digital identity management.
The history of the web and blockchain
To understand the concept of blockchain, we first need to dive into the history of the web.
Web 1.0
The first web was decentralized and free. Anyone could create their own website and store it on their local server at home. The internet did not have a central “governing body” and functioned via protocols (FTP to download data, HTTP to view information in browsers, etc.).
But as the internet grew, so did the IT companies facilitating access to internet resources. Therefore, companies like Google turned into giant corporations that ultimately centralized internet infrastructure.
Web 2.0
Web 2.0 made the internet centralized and platform-based. Today, the most popular platforms (social networks, entertainment websites, or banking services, etc.) belong to just a few large corporations, which store all personal data on their servers. People therefore entrust their private data to several large centers, but this makes users vulnerable.
Although it’s now easier than ever to conduct business online, everything on the web is now controlled by private companies. As a result, our accounts can easily be blocked or otherwise affected because corporations handle content and community moderation on their terms.
The key problems with Web 2.0 are:
- Content does not belong to creators any more.
- Users can lose their content easily, because centralized databases are vulnerable to hacks (your data can be accessed, forged and sold).
- There is too much data leakage. According to Security Magazine, there were more than 4,000 publicly-disclosed breaches that exposed over 22 billion of records in 2021 alone.
Web 3.0
The concept of Web 3.0 is still being developed, but its main idea is a return to decentralization, just like in Web 1.0, and removing “governing bodies” that control content.
Web 3.0 aims to become a peer-to-peer (P2P) network distributed between computers—from personal laptops to company servers. This way, information would be stored on multiple devices which participate equally in supporting the network. In turn, distributed information could never be deleted by, let’s say, a single decision by a corporation’s CEO.
In contrast with Web 2.0, which was originally aimed at content creation by and for humans, Web 3.0 should now be structured in a way that’s also machine-readable. In other words, it will become a “semantic web”.
When data is distributed, trust is vested in nodes (or participating computers), rather than between people (or between the user and a given corporation). The network should therefore make sure that the participating computer does not modify the information.

And here we proceed to the concept of blockchain.
Blockchain
The idea of Web 3.0 emerged with the creation of Bitcoin, which works on blockchain technology.
Blockchain was first described by Satoshi Nakamoto in “Bitcoin: A Peer-to-Peer Electronic Cash System”.
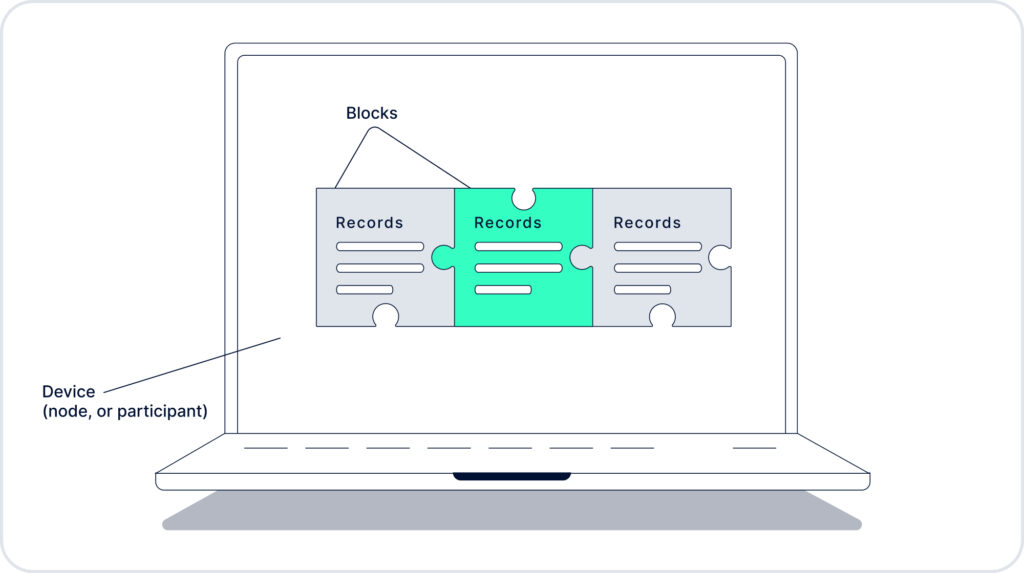
Blockchain is a digital distributed database which can be used to store and transmit digital data, often records of completed transactions. All records in the blockchain are presented in the form of blocks, which are interconnected by special keys. Each new block contains data about the previous one.
Here is how blockchain works in transactions:
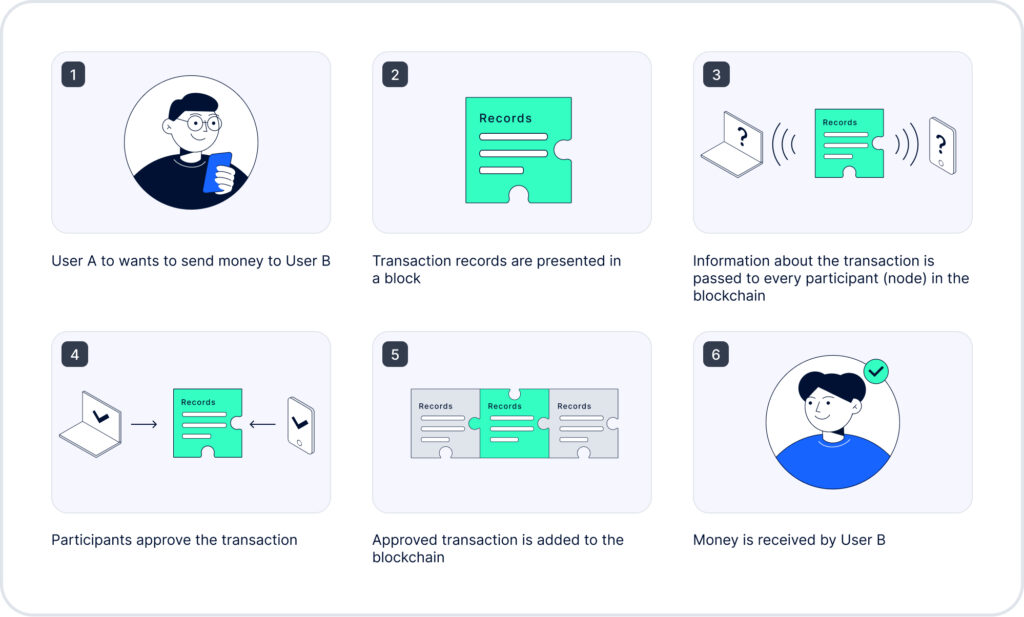
Blockchain consists of the following:
- A list of records. Bitcoin’s blockchain, for example, consists of transactions. Today, however, there are hundreds of blockchain types, which may consist of any information—not just transactions.
- These records are united into blocks. Blocks are connected to each other, and this connection can in no way be broken.
- Each blockchain participant can download the whole chain and personally check that the chain is mathematically correct and there has been no alterations to it.
- Anyone can add a new record to the chain, but only according to a special pattern. Other chain participants monitor that the record has been added correctly.
- Nothing can be deleted—only added.
- When a participant adds a new block, they receive a token as a reward. This token can be used at a crypto exchange, an NFT-market, etc.
- Blockchain can be altered in case of an attack, where 51% of all nodes participating in the chain agree to an alteration. For instance, bad actors can conspire to form a 51% majority, and launch what's called a "51% attack." However, there are mechanisms to prevent such attacks and restore the network if impacted.
The basic principle of blockchain technology can be used in multiple spheres, from banking to digital identity.
Any service in need of a distributed database, which demands establishment of trust between participants can enjoy the database integrity of blockchain. The technology brings us into a new era of digital trust, which is the main problem with Web 2.0.
A good example of the shortcomings of Web 2.0 is how we check our bank account balance. Typically, we open an online banking app to find out. But what prevents the bank from turning the whole amount to zero? In theory, nothing. Even an online account statement is useless if it’s not protected with an electronic signature.
Relationships between clients and institutions are built on trust. This trust can only be supported with reputation, certification, licenses, and references. We are so used to dealing with centralized institutions, like banks, governments, regulators, and big tech, that we entrust them with the most valuable asset we have—our private information. But this trust can easily be betrayed. And this is where blockchain can potentially help by equally distributing such information across different sources, rather than in one vulnerable database.
Blockchain could also help keep personal data private and secure, which brings us to digital identity.
Digital identity on blockchain
A digital identity is online information leading to an existing person or entity. For example, this could be photos on social media, online bank accounts, address on a website, etc.
The main issues with storing digital identity on Web 2.0 are:
- Centralized systems are insecure and may be hacked or otherwise impacted;
- Users don't have complete ownership and control over their data.
Decentralized digital identity on the blockchain can solve these problems, as data can be created, used and stored across multiple participating platforms in a secure and anonymous way (using the private key), so that the user is the only one responsible for their data.
In a decentralized identity framework, users only need a special blockchain software and the internet to access the data.
When information is recorded on a blockchain, its authenticity is ensured by a chain of nodes which support the network. In other words, it requires the majority of chain participants to confirm the validity of all recorded data.
Blockchain for identity management may be used in many ways, but the key takeaway is that private data, especially documents, should not have to be uploaded to public blockchains. This concept guarantees security of personal data.
Decentralized identifiers and verifiable credentials
According to the World Wide Web Consortium, a decentralized identifier is “a portable URL-based identifier, also known as a DID, associated with an entity. These identifiers are most often used in a verifiable credential and are associated with subjects such that a verifiable credential itself can be easily ported from one repository to another without the need to reissue the credential”.
An example of a DID would be “did:123456abcdef”, while a verifiable credential would be digital documents released and cryptographically signed by the issuing entity (like a registry office).
There is still no consensus on how a decentralized identifier would be issued to a person or an entity. Will it be through a trusted institution, like a registry office, or will users create such identifiers themselves using special blockchain software? Either way, Web 3.0 will use decentralized identifiers to verify users.
The Issuer. The Issuer is any third party—a university, hospital, registry office, etc.—which issues documents, or verifiable credentials, to the Holder. These verifiable credentials must have a unique cryptographic signature.
The Verifier. The Verifier is the entity that checks that the credentials of the Holder has from the Issuer are true. For example, the Verifier can be a shop selling alcohol that checks that the customer (Holder) is old enough to drink, or a customs office checking whether a visa is valid, etc.
Trust triangle. To sum up, the following parties are involved in relations on blockchain:
- The Holder
- The Issuer
- The Verifier
The Holder has a wallet where their verifiable credentials are stored. And all three parties must have a special blockchain software through which information can be exchanged and verified.
Public and private keys. To issue data, transactions, or verify the authenticity of information on the blockchain, the above-mentioned parties need to have a public and private key. A public key consists of a sequence of figures and numbers which everyone can download and check, while
A private key is known and held by the owner (Holder) only for accessing private data. If the owner loses their private key, they will never be able to access or use their data.
In order to transfer private data to the Verifier, the Holder needs to use their private key to form the verifiable presentation—in other words, the information needed to complete a given transaction.
To sum up, a blockchain digital identity would allow users, or Holders, to:
- Have control and ownership of their personal data;
- Access and update information;
- Share only certain information with Verifiers for identity verification, and keep the rest of their data private;
- Delete their identity.
Issues with blockchain digital identity
The primary problem of blockchain digital identity is lacking awareness.
Most non-tech users have not yet heard about this technology, while many organizations do not have a complete understanding of how to deploy the decentralized identity technology.
Other important issues include:
- Issues with the “trust triangle”
The “trust triangle” between the Holder, the Issuer and the Verifier may not be reliable, as nothing would prevent the Verifier, for example, from saving the received data and forming another centralized database. Therefore, the concept of SBTs is becoming more popular, as soulbound tokens cannot be transferred.
- Overcoming the legacy systems and regulations
Decentralized identity requires wide changes in legislation, and complex infrastructure on a large scale.
- The possibility of a “51% attack” and a number of other attacks
A “51% attack” is an attack on a blockchain by participants who control more than 50% of the network's hash rate. Owning 51% of the nodes on the network gives the controlling parties the power to alter the blockchain. Among other attacks are the Eclipse attack, Vector76 attack, etc.
However, the blockchain community has mechanisms to defend against these and other attacks, as well as restore a harmed network.
- Connecting digital identities with the real people and entities
Blockchain cannot guarantee the physical identity of the user. Institutions would need to agree on a mechanism that would check that data stored on blockchain belongs to a real person.
FAQ
-
What is a digital identity on blockchain?
A digital identity on blockchain can either be a self-sovereign identity, allowing users to share a limited part of their data with a verifying party, or an SBT-based identity which would prove that a given user has passed KYC.
-
How does blockchain create and use a digital identity?
Blockchain creates decentralized identifiers which can be associated with individuals (identities).
-
How long does it take blockchain to verify identity?
According to the Blockchain Support Center, it takes from 5 minutes to 2 hours. If a manual check is required, it may take around 5 business days.
-
How can blockchain be used for authentication?
Users can be verified or authenticated either through the self-sovereign identity, when the user, or the holder, shares part of data with the verifier, or through soulbound tokens (SBT).
-
Can blockchain prevent identity theft?
On the one hand, blockchain digital identity is designed in such a way that only the owner can access their data. On the other hand, an attack against blockchain may be a threat. However, such attacks can be prevented, and the work of the network can be restored.
-
Can blockchain protect data confidentiality?
Blockchain enables data to be shared in ways that maintain an individual’s privacy and control over their own data.
Relevant articles
- Article
- 2 days ago
- 11 min read
Check out how AI deepfakes are evolving and discover proven strategies for detecting and preventing deepfake threats to protect your business.

- Article
- Jan 15, 2026
- 8 min read
AI-generated fake IDs are bypassing traditional KYC: learn why businesses need to rethink their identity verification in 2026.
What is Sumsub anyway?
Not everyone loves compliance—but we do. Sumsub helps businesses verify users, prevent fraud, and meet regulatory requirements anywhere in the world, without compromises. From neobanks to mobility apps, we make sure honest users get in, and bad actors stay out.